Malcolm
A Network Traffic Analysis Tool Suite
Idaho National Laboratory partners with the Department of Homeland Security’s Cybersecurity Infrastructure Security Agency (CISA) to defend against today’s threats and collaborates to build a more secure and resilient infrastructure for the future.
INL’s national and homeland security expertise and capabilities support CISA with research and development of technologies, tools, and training to stay ahead of evolving cyber and physical threats. This effort supports all 16 critical infrastructure sectors that are important to the functioning of our country and everyday lives, including communications, energy, transportation and water.
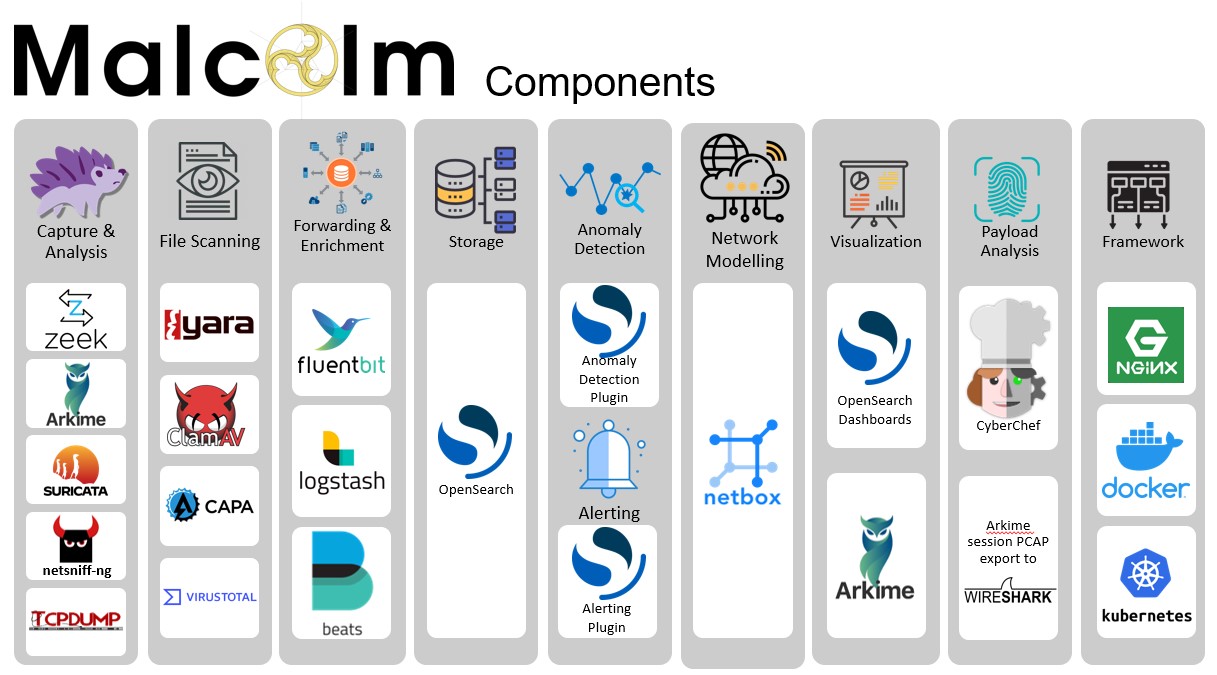
One outcome of this collaboration is Malcolm, a powerful open-source network traffic analysis tool suite. Although all the open-source tools that make up Malcolm are already available and in general use, Malcolm provides a framework of interconnectivity that makes it greater than the sum of its parts. And while there are many other network traffic analysis solutions out there, ranging from complete Linux distributions like Security Onion to licensed products like Splunk Enterprise Security, Malcolm’s creators feel its easy deployment and robust combination of tools fill a void in the network security space that will make network traffic analysis accessible to many in both the public and private sectors as well as individual enthusiasts.
Malcolm Capabilities and Assets
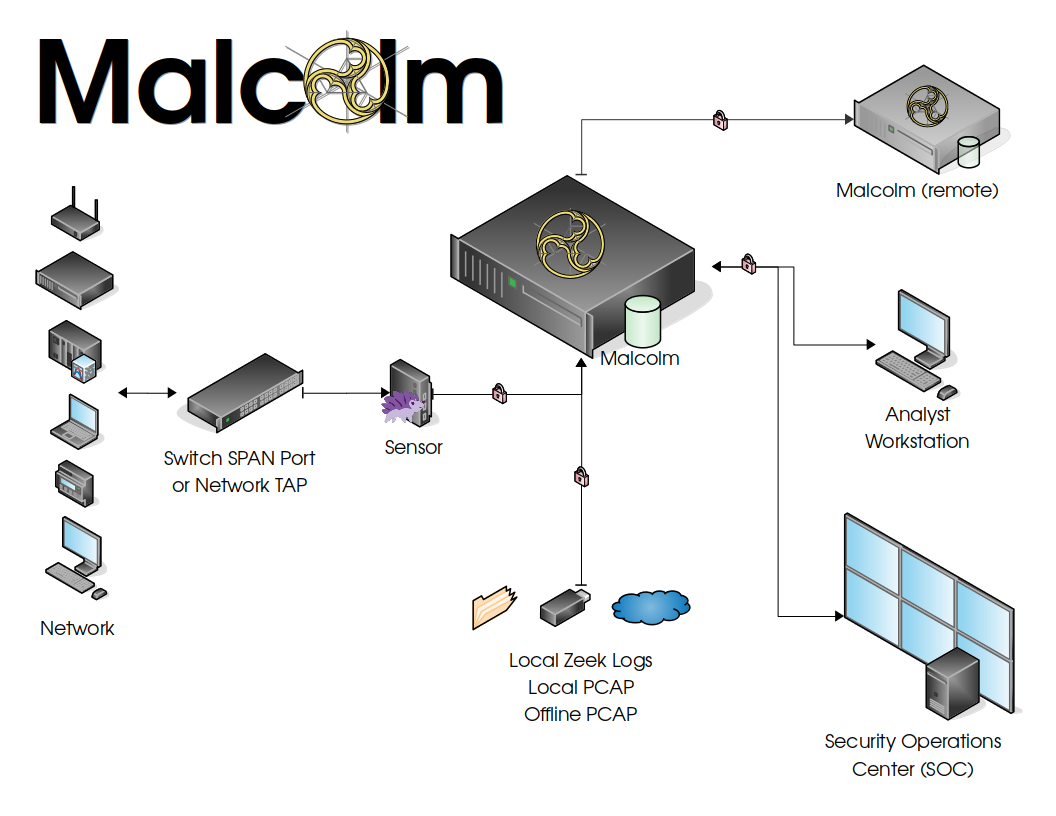
- Easy to use – Malcolm accepts network traffic data in the form of full packet capture (PCAP) files and Zeek (formerly Bro) logs. These artifacts can be uploaded via a simple browser-based interface or captured live and forwarded to Malcolm using lightweight forwarders. In either case, the data is automatically normalized, enriched and correlated for analysis.
- Powerful traffic analysis – Visibility into network communications is provided through two intuitive interfaces: Kibana, a flexible data visualization plug-in with dozens of prebuilt dashboards providing an at-a-glance overview of network protocols; and Arkime (formerly Moloch), a powerful tool for finding and identifying the network sessions comprising suspected security incidents.
- Streamlined deployment – Malcolm operates as a cluster of Docker containers, isolated sandboxes that each serve a dedicated function of the system. This Docker-based deployment model, combined with a few simple scripts for setup and run-time management, makes Malcolm suitable to be deployed quickly across a variety of platforms and use cases, whether it be for long-term deployment on a Linux server in a security operations center or for incident response on a MacBook for an individual engagement.
- Secure communications – All communications with Malcolm, both from the user interface and from remote log forwarders, are secured with industry standard encryption protocols.
- Permissive license – Comprised of several widely used open-source tools, Malcolm is an attractive alternative to security solutions requiring paid licenses.
- Expanding control systems visibility – While Malcolm is great for general-purpose network traffic analysis, its creators see a particular need in the community for tools providing insight into protocols used in industrial control systems (ICS) environments. Ongoing Malcolm development will aim to provide additional parsers for common ICS protocols.
Malcolm provides an easily deployable suite of tools for full packet capture artifacts (PCAP files) and Zeek logs. While Internet access is required to build it, it is not required to run.
Malcolm Tutorials and Resources
Custom IT architecture design and software development for infrastructure applications serves to solve complex challenges in critical infrastructure protection. These innovative applications are developed using modeling and simulation, information system analytics, and host data. Subject matter experts administer these certified applications and safely handle protected critical infrastructure information, sensitive regulatory and proprietary data.
Participating Laboratories
Idaho National Laboratory is a world leader in providing industrial control system cybersecurity research and development. The laboratory’s distinctive history in protecting critical infrastructure systems puts the lab at the forefront of thought leadership and applied innovation in critical infrastructure cybersecurity testing. INL uses a comprehensive approach to developing ICS cybersecurity research to meet the energy sector’s needs identified by DOE, utilities and other organizations. >> Read more on INL National Security