Controls Laboratory
Environment for cyber research of operational technologies
The Controls Laboratory is an environment for government and private industry partners to experience the possible effects of kinetic cyber-physical attacks. This lab allows users to perform security research on industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems.
The Controls Laboratory is an environment for government and private industry partners to experience the real-world impacts of cyber-physical attacks. It supports security research on industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. The laboratory facilitates the study of cyber warfare against our nation’s critical infrastructure (CI) targets, which are essential for sustaining our society’s way of life.
This adaptable lab simulates various corporate network configurations and provides control system hardware and kinetic outputs across CI sectors. It can host multiple concurrent simulations, enabling analysts nationwide to interact both on-site and remotely via extended range connections.
Distinguishing assets and capabilities
What’s unique about our environment?
- Combines functional ICS/SCADA systems with threat actor tactics, techniques and procedures (TTPs).
- Hosts simulations for both red and blue teams to experience specific threat actor TTPs.
- Shows disruptive and destructive consequences of cyberattacks against ICS and how to defend against them.
The core capabilities of the range include:
- Studying red team capabilities, techniques, artifacts, and impacts within specific network configurations.
Enabling blue teams to hone defensive skills and develop new processes for detecting malicious cyber activity.
Validating and understanding the impact of vulnerabilities within ICS hardware and configurations.
This lab focuses on ICS technologies and simulating cyberattacks that cause physical disruption and destruction. It integrates kinetic motion in attack scenarios to address infrastructure interdependencies. The real-time response capability enables support for teams throughout the entire cyberattack life cycle, including internet entry points, external demilitarized zones, corporate local area networks, ICS networks and physical components.

Waste water
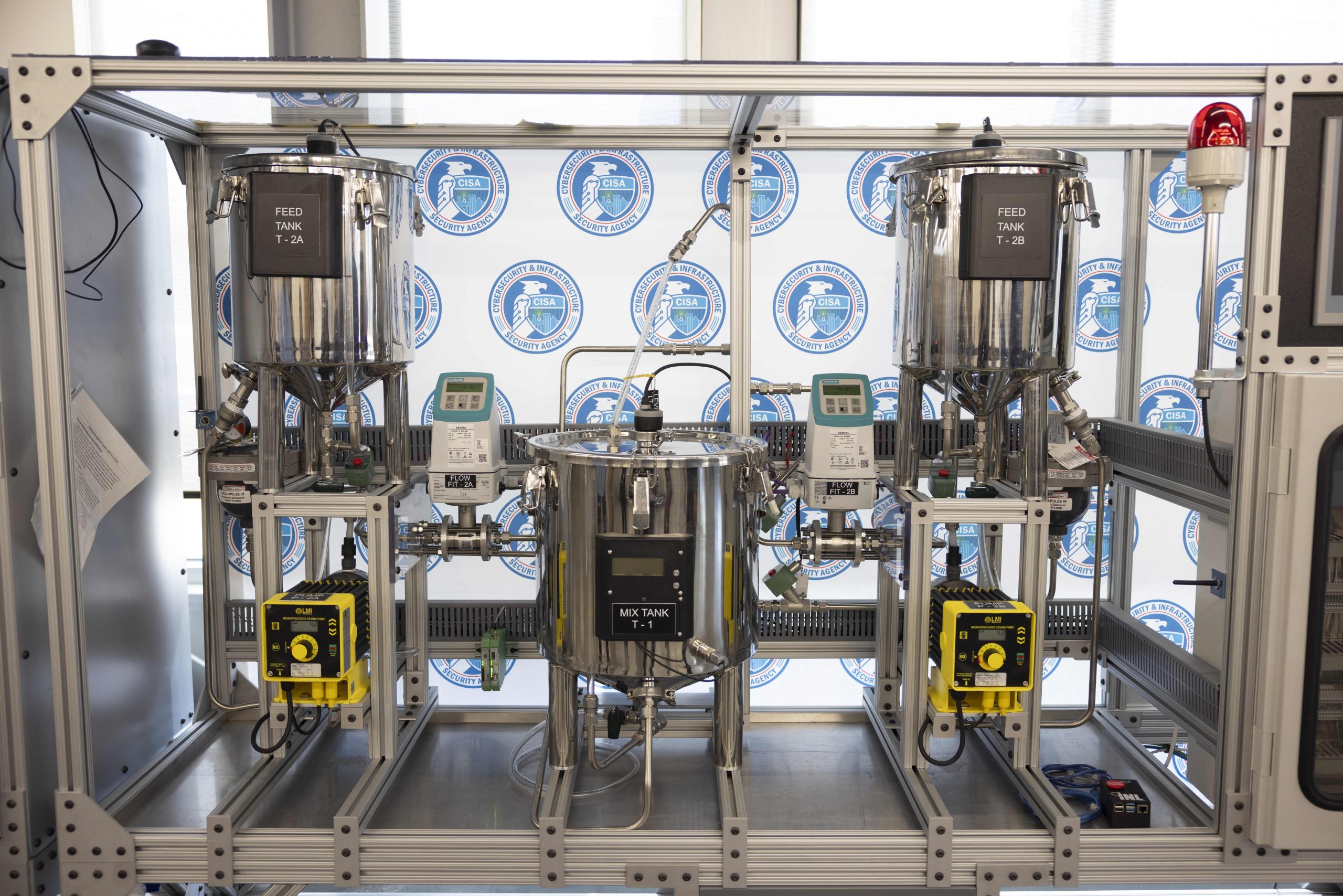
Chemical processing

Electrical distribution and transmission

Natural gas pipeline

Building management
Virtual Tour
Who can use this lab?
This research zone allows users to simulate risk scenarios without affecting production environments. It helps government and industry partners enhance ICS network defenses. Potential users include:
- Federal civilian agencies (e.g., Department of Energy, Justice, Interior)
- Department of Defense Cyber Protection Teams (CPTs)
- National Security Agency
- U.S. asset owner operators
- Vendors and integrators
- Academia researchers
- Third-party cyber firms and researchers
- International partners
Designed for critical infrastructure partners, the test bed serves various industry groups, providing a space to research, learn, and share TTPs.
User assets
- Concurrent simulations for diverse user groups.
- Customized corporate environments for all business sizes.
- Representative sector-specific skid scenarios.
- Remote access to simulations.

Tutorials and use cases
The videos below offer additional information on the Controls Laboratory and its use in training cybersecurity professionals on ICS and OT environments. These presentations were given at previous Industrial Control System Joint Working Group (ICS-JWG) seminars to facilitate information sharing and reduce risks to the nation’s industrial control systems. Sponsored by the Cybersecurity and Infrastructure Security Agency (CISA), the ICS-JWG promotes communication and partnerships across all critical infrastructure (CI) sectors. The goal is to secure CI by accelerating the design, development and deployment of secure industrial control systems.
