The Headgate Rock Dam holds back about 7,000 acre-feet of water from the lower Colorado River in Lake Moovalya — an oasis in a hot and dusty corner of southwest Arizona.
Not only does the dam provide electricity and irrigation for the surrounding Colorado River Indian Reservation Farms, but it protects downstream communities from the uncontrolled release of water.
The dam is one of hundreds of critical infrastructure facilities in far-flung locations throughout the U.S. with an urgent need for robust cybersecurity. Modern infrastructures — including dams and reservoirs — rely on connected sensors, wireless enabled values and meters, and floodgates that are networked to computer systems.
“The Bureau of Reclamation has all of these hydroelectric facilities, and some are quite remote,” said Seth Grover, a cybersecurity researcher at Idaho National Laboratory. “Enticing network security experts to live in Parker, Arizona, is challenging. They had staffing issues.”
Instead, the department partnered with the Cybersecurity and Infrastructure Security Agency (CISA) and asked INL to develop an inexpensive cybersecurity solution that could analyze network traffic and identify malicious code before a cyberattack damages critical infrastructure.
Threat analysis information generated by the program is then scrutinized by a human security analyst working from another location.
Combining existing cybersecurity tools
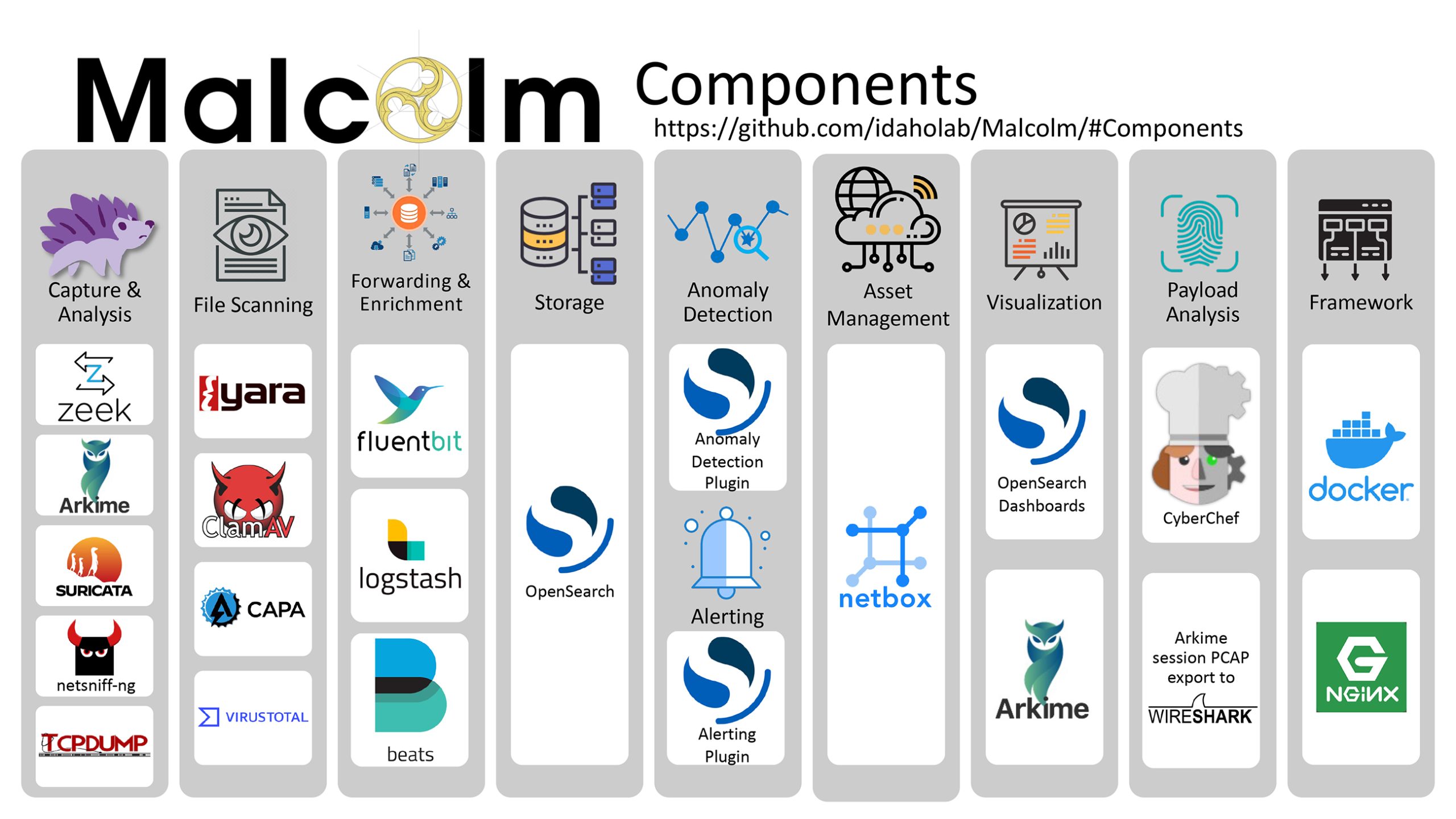
The software that Grover and his colleagues developed was the first iteration of Malcolm, a framework that incorporates several existing, open-source cybersecurity tools into one low-cost solution. The owners of open-source software release it for free so it can be redistributed and modified.
Malcolm — named after the chaos theory scientist played by Jeff Goldblum in the film “Jurassic Park” — is designed to analyze high-volume network traffic to detect malicious activity. “Malcolm takes this unpredictable chaotic mess and applies order to it,” Grover said.

The framework is adaptable and specialized. It’s one of the only cybersecurity solutions designed to analyze network traffic of operational control technology, the type of technology used to open things like a floodgate in a dam, or turn off a pump on natural gas pipeline or water treatment plant.
Malcolm’s strength is its reliance on an ever-evolving suite of cybersecurity tools.
“It’s a combination of open-source, industry-standard tools that are trusted, with a lot of special sauce and glue that maximizes their ability to work together,” Grover said. “If you install one of those off-the-shelf tools in your operational technology network, you might see what the programmable logic controller that operates your dam is doing.”
Malcolm bridges the gap
Take, for example, two of the tools — Zeek and Arkime — that lie at the heart of the Malcolm framework.
Zeek captures and summarizes network traffic, logging the salient application-layer metadata without getting caught up in minutiae. Conversely, Arkime links each indexed network session to its source in the traffic stream, allowing an analyst to visualize the original payload.
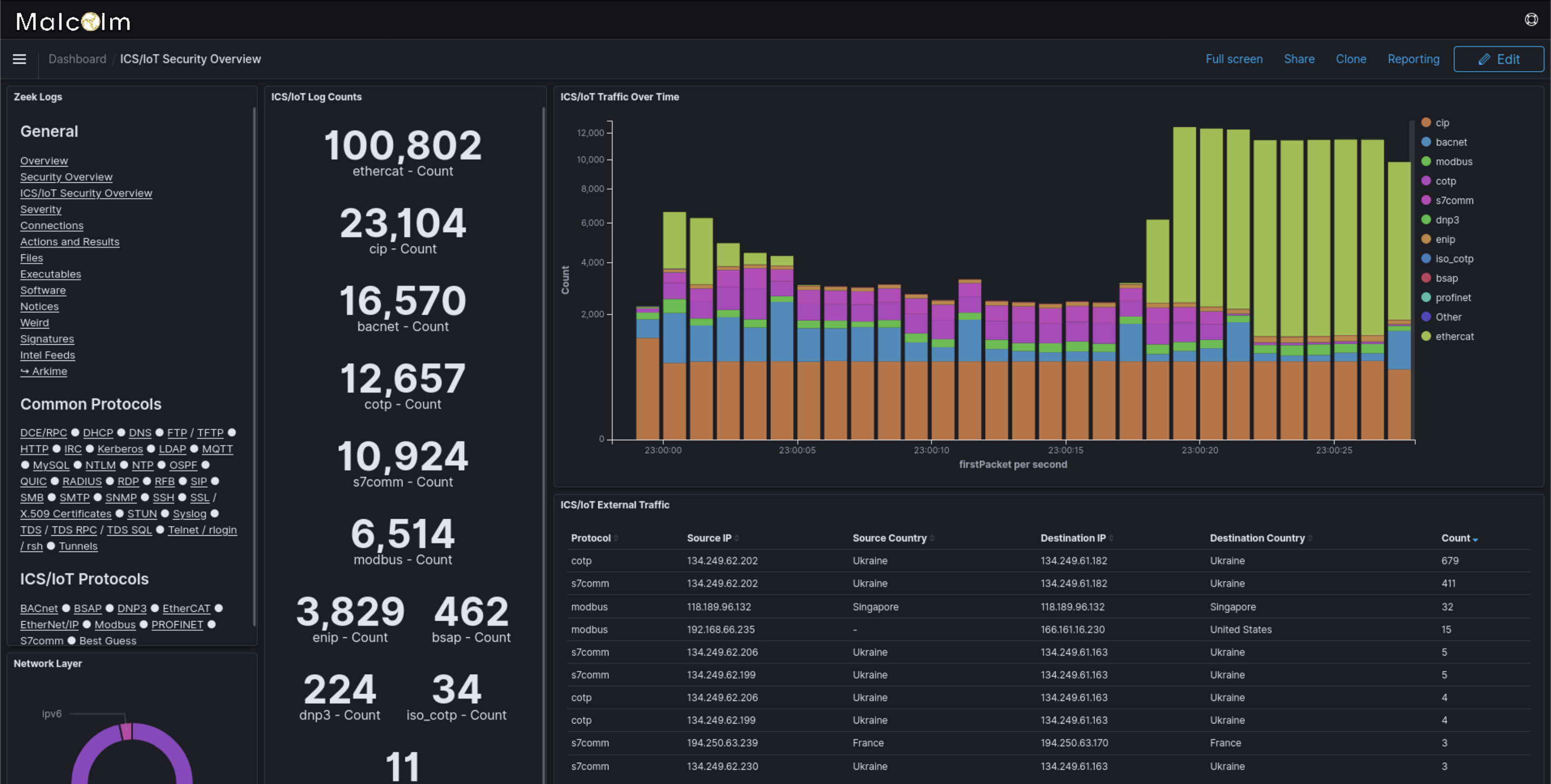
“Malcolm bridges that gap,” Grover said. “Someone might start at a 10,000-foot view with the Zeek logs to identify something of interest. Malcolm facilitates pivoting from that 10,000-foot summary to the finer detail of Arkime.”
The key to Malcolm is using multiple types of open-source software and keeping the platform relevant by collaborating with the cybersecurity community.
Another route for detecting possible cyberattacks is using machine learning and artificial intelligence to detect deviations from normal behaviors. Typically, most types of operational control systems perform the same kind of tasks repeatedly. Using anomaly detection techniques, Malcolm identifies deviations that cybersecurity analysts might not know they were looking for.
A new addition is Suricata, which a senior capstone project team at Brigham Young University integrated into Malcolm. Suricata seeks patterns in the raw network stream, similar to how antivirus software scans a personal computer, but it scans network traffic rather than documents and files.
Recognizing the value of these types of capabilities, CISA has continued to work with INL to advance solutions that meet the core cybersecurity needs of U.S. critical infrastructure asset owners and our partners around the world.
For instance, a team of researchers in Germany is incorporating Malcolm into an initiative by the Federal Ministry of Interior and Community, the agency tasked with managing the nation’s computer and communications security.
Powerful and extremely affordable
Zeek, Arkime and Suricata are three of more than a dozen open-source tools that Grover and his colleagues have incorporated into Malcolm, making the framework powerful and extremely affordable.
Grover was recently awarded “Best Contribution to the Zeek Community” by the Corelight Apex Awards, from the makers of Zeek.

“I’m a big open-source advocate,” Grover said. “When we’re talking about using taxpayer dollars, it ought to benefit as many people as possible.”
“I really wanted to find similar projects addressing these network security problems,” he continued. “Some tools are good at some things, but deficient in others. They all do a different piece. I want to make it as easy to package these tools together, whether it’s for a ma-and-pa-sized operation at a municipality or a federal agency like the U.S. Bureau of Reclamation.”
For more information, visit: https://inl.gov/ics-malcolm.